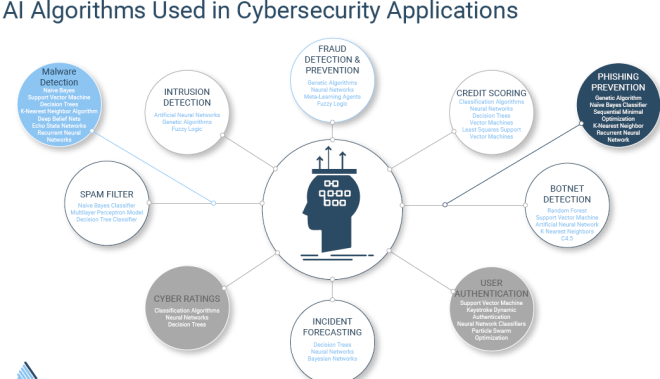
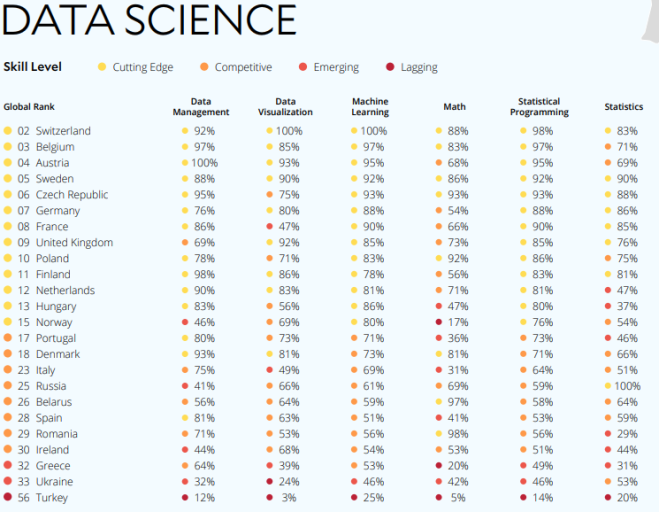
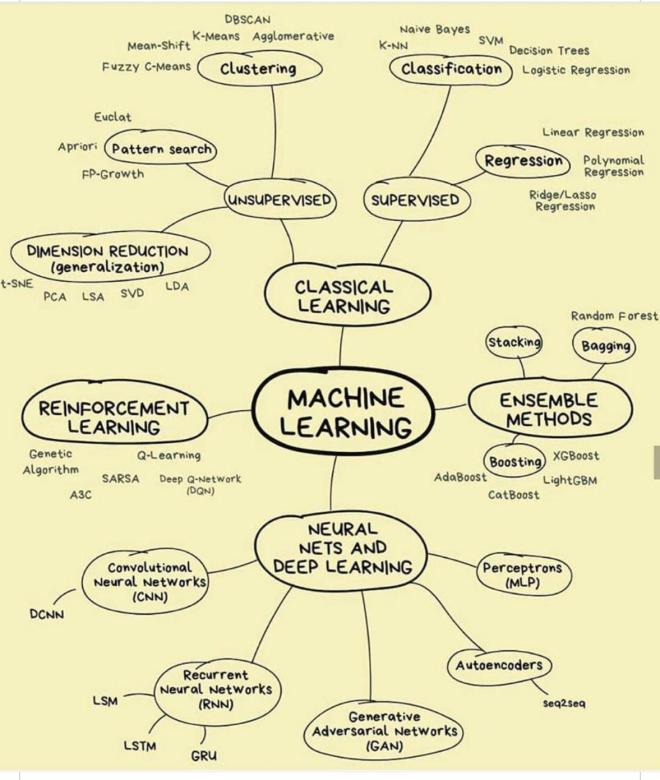
Internet of Things—Architecture

The basis for the IoT Reference Architecture structuring approach.
• Functional – Describes the system’s runtime functional elements and their responsibilities, interfaces , and primary interactions
• Information – Describes the way that the architecture stores, manipulates, manages, and distributes data and information.
• Deployment – Describes the environment into which the system will be deployed, including the dependencies the system has on its runtime environment
• Operational – Describes how the system will be operated, administered, and supported when it is running in it s production environment
Quality aspects of the IoT reference architecture are addressed through definitions of perspectives. The perspectives and their definition are provided in the following list:
• Security and privacy – Provides and analysis of the security threads in the functionality groups of the architecture and gives an explanation how security and privacy concerns should be addressed.
• Performance and scalability – Provides the ability of the system to handle a large number of devices, services and processes in an efficient way. Further more, the fluctuation of requests towards those has to be handled in a scalable way.
• Availability and resilience – The ability of the system to be fully or partly operational as and when required, and to effectively handle failures that could affect system availability
• Evolution and interoperability – The ability of the system to be flexible in the face of the inevitable change that all systems experience after deployment; the ability of two or more systems or components to exchange and use information
Field of application : Transportation/ Logistics

Impacts:
In transport logistics, IoT improves not only material flow systems, but also global positioning and auto identification of freights. Additionally, it increases energy efficiency and decreases thus e nergy consumption. In conclusion, IoT is expected to bring profound chan ges to the global supply chain via intelligent cargo movement. This will be achieved by means of continuous process synchronisation of supply-chain information, and seamless real-time tracking and tracing of objects. It will provide the supply chain a transparent, visible and controllable nature, enabling intelligent communication between people and cargo.
Field of application : Smart home

Impacts:
Future smart homes will be conscious about what happens inside a building, mainly impacting three aspects: re source usage (water conservation and energy consumption), security, and comfort. The goal with all this is to achieve better levels of comfort while cutting overall expenditure. Moreover, smart homes also address security issues by means of complex security systems to detect theft, fire or unauthorized entries. The stakeholders involved in this scenario constitute a very heterogeneous group. There are different actors that will cooperate in the user’s home, such as Internet companies, device manufacturers, telecommunications operators, media-service providers, security companies, electric-utility companies, etc.
Field of application : Smart city

Impacts:
While the term smart city is still a fuzzy concept, there is a general agreement that it is an urban area wh ich creates sustainable development and high quality of life. Giffinger et al .’s model elucidates the characteristics of a smart city, encompasing economy, people, governance, mobility, environment and living [Giffinger, 2007]. Outperforming in these key areas can be done through strong human or social capital and/or ICT infrastructure. For the latter, a first business analysis concludes that several sectors/industries will benefit from more digitalised and intelligent cities (examples for a city of 1 milli on people [Nicholson, 2010]): • Smart metering, 600.000 meters, US $ 120 million opportunity • Infrastructure for charging electric vehicles, 45.000 electric vehicles, US $ 225 million opportunity • Remote patient monitoring (diabetes), 70.000 people, US $ 14 million opportunity • Smart retail, 4.000 stores, US $ 200 million opportunity • Smart-bank branches, 3.200 PTMs, US $ 160 million opportunity
Field of application :Smart factory

Impacts:
Companies will be able to track al l their products by means of RFID tags by means of a global supply chain; as a consequence, companies will reduce their OPEX and improve thei r productivity due to a tighter integration with ERP and other systems. Generally, IoT will provide automatic procedures that imply a drastic reduction in t he number of employees needed. Workers will be replaced by bar-code scanners, readers, sensors and actuators, and in the end by complex robots, as much efficient as a hu man. Without any doubt, these technologies will bring opportunities for white-collar workers and a big number of technicians will be necessary to program and repair these machines. This is synonymous to a transfer to maintenance jobs, but it also constitutes a new challenge for providing all blue-collar workers with an opportunity to move toward these types of jobs and to avoid unemployment.
Field of application : Retail

Impacts :
IoT realises both customer needs and business needs. Price comparison of a product; or looking for other products of the same quality at lower prices, or with shop promotions gives not only information to customers but also to shops and business. Having this informat ion in real time helps enterprises to improve their business and to satisfy customer needs. Obviously, big retail chai ns will take advantage of their dominant position in order to enforce the future IoT reta il market, as it happened with RFID adoption, which was enforced by WalMart in 2004 [Field, 2008]. Particularly, companies with controlling positions, such as WalMart, Carrefour, Metro AG, etc. are able to push the adoption of IoT technology due to their sizable market shares.
Field of Application : eHealth

Impacts :
Controlling and preventing is one of the main goals of future health care. Already today, people can have the possibility of being tracked and monitored by specialists even if both are not at the same place. Tracing peoples’ health history is another aspe ct that makes IoT-assisted eHealth very versatile. Business applications could offer the possibility of medical service not only to patients but also to specialists, who need information to proceed in their medical evaluation. In this domain, IoT makes human interaction much more efficient because it not only permits localization, but also tracking and monitoring of patient s. Providing information about the state of a patient makes the whole process more efficient, and also makes people much more satisfied. The most important stakeholders in th is scenario will be public and private hospitals and institutes such as, e.g ., the Institute of Applied eHealth at Edinburgh Napier University, which partook in the fi rst stakeholder session of IoT-A. It is worth mentioning that telecommunications operators are quite active in e-health (for instance, O2 UK).
Field of Application : Environment

Impacts :
From the aforementioned application we infe r that environment has many overlaps with other scenarios, such as smart home and smart city. The key issue in these scenarios is to detect mean s that help to save energy. We are basically referring to what is known as Smart Grid. Concerning this application area one needs to highlight initiatives that imply a more distributed energy production, since many houses have a solar panel today. As a vital part, smart metering is co nsidered as a pre-condition for enabling intelligent monitoring, control, and communication in grid applications. The use of IoT platforms in Smart Metering will provide the following benefits: • An efficient network of smart mete rs allows for faster outage detection and restoration of service. Such c apabilities redound to the benefit of customers • Provides customers wi th greater control over their energy or water consumption, providing them more choices for managing their bills. • IoT deployment of smart meters is expected to reduce the need to build power plants. Building power pl ants that are necessary only for occasional peak demand is very expensive. A more economical approach is to enable customers to reduce their demand through time-based rates or other incentive programs, or to use automatic recording of consumptions to turn off devices temporarily which are not in use. Finally, combining the analysis of supply and demand, energy enterprises will able to supply a more efficient dem and shaping. They will not just give incentives to consumers, but actually turning off devices that are not needed (like the freezer for 20 minutes). Also most of this needs to happen automatically.Here we again face a heterogeneous scenario, in which diverse stakeholders are involved. Main actors are of course energy utilities, but also public entities will be important players.